Shared security patch analysis results
AI Used: DEEPSEEK deepseek-chat--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/testing/web-platform/tests/html/canvas/offscreen/shadows/2d.shadow.stroke.join.3.worker.js+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/testing/web-platform/tests/html/canvas/offscreen/shadows/2d.shadow.stroke.join.3.worker.js@@ -13,8 +13,8 @@ }); t.step(function() {-var offscreenCanvas = new OffscreenCanvas(100, 50);-var ctx = offscreenCanvas.getContext('2d');+var canvas = new OffscreenCanvas(100, 50);+var ctx = canvas.getContext('2d'); ctx.fillStyle = '#0f0'; ctx.fillRect(0, 0, 100, 50);@@ -29,10 +29,10 @@ ctx.lineTo(-150, -50); ctx.lineTo(-151, -100); // (not an exact right angle, to avoid some other bug in Firefox 3) ctx.stroke();-_assertPixel(offscreenCanvas, 1,1, 0,255,0,255, "1,1", "0,255,0,255");-_assertPixel(offscreenCanvas, 48,48, 0,255,0,255, "48,48", "0,255,0,255");-_assertPixel(offscreenCanvas, 50,25, 0,255,0,255, "50,25", "0,255,0,255");-_assertPixel(offscreenCanvas, 98,48, 0,255,0,255, "98,48", "0,255,0,255");+_assertPixel(canvas, 1,1, 0,255,0,255, "1,1", "0,255,0,255");+_assertPixel(canvas, 48,48, 0,255,0,255, "48,48", "0,255,0,255");+_assertPixel(canvas, 50,25, 0,255,0,255, "50,25", "0,255,0,255");+_assertPixel(canvas, 98,48, 0,255,0,255, "98,48", "0,255,0,255"); t.done(); });
Based on the provided diff, I don't see any security vulnerabilities being fixed. The changes appear to be purely variable renaming (from `offscreenCanvas` to `canvas`) and the corresponding updates to the assertions. Here's the analysis following your format:
Vulnerability Existed: no
No security vulnerability found [testing/web-platform/tests/html/canvas/offscreen/shadows/2d.shadow.stroke.join.3.worker.js] [Lines 13-29]
[Old Code]
var offscreenCanvas = new OffscreenCanvas(100, 50);
var ctx = offscreenCanvas.getContext('2d');
...
_assertPixel(offscreenCanvas, 1,1, 0,255,0,255, "1,1", "0,255,0,255");
[Fixed Code]
var canvas = new OffscreenCanvas(100, 50);
var ctx = canvas.getContext('2d');
...
_assertPixel(canvas, 1,1, 0,255,0,255, "1,1", "0,255,0,255");
The changes are purely cosmetic/refactoring in nature and don't appear to address any security issues. The functionality remains exactly the same, just with a different variable name.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/security/nss/lib/ssl/ssl3ext.c+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/security/nss/lib/ssl/ssl3ext.c@@ -55,7 +55,6 @@ { ssl_tls13_psk_key_exchange_modes_xtn, &tls13_ServerHandlePskModesXtn }, { ssl_tls13_cookie_xtn, &tls13_ServerHandleCookieXtn }, { ssl_tls13_post_handshake_auth_xtn, &tls13_ServerHandlePostHandshakeAuthXtn },- { ssl_tls13_ech_is_inner_xtn, &tls13_ServerHandleEchIsInnerXtn }, { ssl_record_size_limit_xtn, &ssl_HandleRecordSizeLimitXtn }, { 0, NULL } };@@ -83,6 +82,7 @@ static const ssl3ExtensionHandler helloRetryRequestHandlers[] = { { ssl_tls13_key_share_xtn, tls13_ClientHandleKeyShareXtnHrr }, { ssl_tls13_cookie_xtn, tls13_ClientHandleHrrCookie },+ { ssl_tls13_encrypted_client_hello_xtn, tls13_ClientHandleHrrEchXtn }, { 0, NULL } };@@ -167,6 +167,7 @@ { ssl_tls13_key_share_xtn, &tls13_ServerSendHrrKeyShareXtn }, { ssl_tls13_cookie_xtn, &tls13_ServerSendHrrCookieXtn }, { ssl_tls13_supported_versions_xtn, &tls13_ServerSendSupportedVersionsXtn },+ { ssl_tls13_encrypted_client_hello_xtn, &tls13_ServerSendHrrEchXtn }, { 0, NULL } };@@ -277,7 +278,7 @@ return SECSuccess; }-static sslCustomExtensionHooks *+sslCustomExtensionHooks * ssl_FindCustomExtensionHooks(sslSocket *ss, PRUint16 extension) { PRCList *cursor;@@ -322,6 +323,14 @@ const TLSExtensionData *xtnData = &ss->xtnData; return arrayContainsExtension(xtnData->advertised, xtnData->numAdvertised, ex_type);+}++PRBool+ssl3_ExtensionAdvertisedClientHelloInner(const sslSocket *ss, PRUint16 ex_type)+{+ const TLSExtensionData *xtnData = &ss->xtnData;+ return arrayContainsExtension(xtnData->echAdvertised,+ xtnData->echNumAdvertised, ex_type); } /* Go through hello extensions in |b| and deserialize@@ -514,11 +523,21 @@ * do not have any response, so we rely on * ssl3_ExtensionAdvertised to return false on the server. That * results in the server only rejecting any extension. */- if (!allowNotOffered && (extension->type != ssl_tls13_cookie_xtn) &&- !ssl3_ExtensionAdvertised(ss, extension->type)) {- (void)SSL3_SendAlert(ss, alert_fatal, unsupported_extension);- PORT_SetError(SSL_ERROR_RX_UNEXPECTED_EXTENSION);- return SECFailure;+ if (!allowNotOffered && (extension->type != ssl_tls13_cookie_xtn)) {+ if (!ssl3_ExtensionAdvertised(ss, extension->type)) {+ SSL_TRC(10, ("Server sent xtn type=%d which is invalid for the CHO", extension->type));+ (void)SSL3_SendAlert(ss, alert_fatal, unsupported_extension);+ PORT_SetError(SSL_ERROR_RX_UNEXPECTED_EXTENSION);+ return SECFailure;+ }+ /* If we offered ECH, we also check whether the extension is compatible with+ * the Client Hello Inner. We don't yet know whether the server accepted ECH,+ * so we only store this for now. If we later accept, we check this boolean+ * and reject with an unsupported_extension alert if it is set. */+ if (ss->ssl3.hs.echHpkeCtx && !ssl3_ExtensionAdvertisedClientHelloInner(ss, extension->type)) {+ SSL_TRC(10, ("Server sent xtn type=%d which is invalid for the CHI", extension->type));+ ss->ssl3.hs.echInvalidExtension = PR_TRUE;+ } } /* Check that this is a legal extension in TLS 1.3 */@@ -631,7 +650,7 @@ return SECFailure; }-static SECStatus+SECStatus ssl_CallCustomExtensionSenders(sslSocket *ss, sslBuffer *buf, SSLHandshakeType message) {@@ -690,6 +709,7 @@ buf->len += len; if (message == ssl_hs_client_hello ||+ message == ssl_hs_ech_outer_client_hello || message == ssl_hs_certificate_request) { ss->xtnData.advertised[ss->xtnData.numAdvertised++] = hook->type; }@@ -719,6 +739,7 @@ /* Clear out any extensions previously advertised */ ss->xtnData.numAdvertised = 0;+ ss->xtnData.echNumAdvertised = 0; switch (message) { case ssl_hs_client_hello:@@ -803,6 +824,9 @@ } if (!PR_CLIST_IS_EMPTY(&ss->extensionHooks)) {+ if (message == ssl_hs_client_hello && ss->opt.callExtensionWriterOnEchInner) {+ message = ssl_hs_ech_outer_client_hello;+ } rv = ssl_CallCustomExtensionSenders(ss, buf, message); if (rv != SECSuccess) { goto loser;@@ -890,7 +914,9 @@ } else { tailLen = 0; }-+ if (exType == ssl_tls13_encrypted_client_hello_xtn) {+ ss->xtnData.echXtnOffset = buf->len;+ } rv = sslBuffer_AppendNumber(buf, exType, 2); if (rv != SECSuccess) { return SECFailure; /* Code already set. */@@ -952,7 +978,7 @@ while (!PR_CLIST_IS_EMPTY(src)) { cur_p = PR_LIST_TAIL(src); PR_REMOVE_LINK(cur_p);- PR_APPEND_LINK(cur_p, dst);+ PR_INSERT_LINK(cur_p, dst); } }@@ -995,6 +1021,8 @@ ++advertisedMax; } xtnData->advertised = PORT_ZNewArray(PRUint16, advertisedMax);+ xtnData->echAdvertised = PORT_ZNewArray(PRUint16, advertisedMax);+ xtnData->peerDelegCred = NULL; xtnData->peerRequestedDelegCred = PR_FALSE; xtnData->sendingDelegCredToPeer = PR_FALSE;@@ -1017,6 +1045,7 @@ xtnData->certReqAuthorities.arena = NULL; } PORT_Free(xtnData->advertised);+ PORT_Free(xtnData->echAdvertised); tls13_DestroyDelegatedCredential(xtnData->peerDelegCred); tls13_DestroyEchXtnState(xtnData->ech);
Here's the security analysis following the specified format: 1. Vulnerability Existed: yes TLS Encrypted Client Hello (ECH) Handling [security/nss/lib/ssl/ssl3ext.c] [Lines 55, 83, 167, 277, 323, 514, 650, 709, 824, 914, 978, 1021] [Old Code] - Missing ECH extension handling in helloRetryRequestHandlers - Missing ECH extension handling in helloRetryRequestSenders - Static function ssl_FindCustomExtensionHooks - No ECH-specific extension advertised checking - No ECH outer client hello handling - No ECH extension offset tracking - PR_APPEND_LINK used for list operations [Fixed Code] - Added ECH extension handlers for helloRetryRequest - Added ECH extension senders for helloRetryRequest - Made ssl_FindCustomExtensionHooks non-static - Added ssl3_ExtensionAdvertisedClientHelloInner - Added ssl_hs_ech_outer_client_hello handling - Added echXtnOffset tracking - Changed to PR_INSERT_LINK for safer list operations 2. Vulnerability Existed: yes Memory Management [security/nss/lib/ssl/ssl3ext.c] [Lines 1021, 1045] [Old Code] - Missing free for echAdvertised array - Missing initialization of echAdvertised array [Fixed Code] - Added PORT_Free(xtnData->echAdvertised) - Added initialization of echAdvertised array 3. Vulnerability Existed: not sure Potential Race Condition [security/nss/lib/ssl/ssl3ext.c] [Lines 978] [Old Code] PR_APPEND_LINK(cur_p, dst) [Fixed Code] PR_INSERT_LINK(cur_p, dst) Additional Details: The change in list operation method might indicate a potential race condition fix, but without more context about the threading model, this is uncertain. The changes primarily focus on improving Encrypted Client Hello (ECH) support and fixing related memory management issues. The ECH-related changes appear to address potential security issues in the TLS handshake process when dealing with encrypted client hello messages.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/testing/web-platform/tests/html/canvas/offscreen/fill-and-stroke-styles/2d.pattern.basic.image.html+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/testing/web-platform/tests/html/canvas/offscreen/fill-and-stroke-styles/2d.pattern.basic.image.html@@ -17,8 +17,8 @@ }); t.step(function() {-var offscreenCanvas = new OffscreenCanvas(100, 50);-var ctx = offscreenCanvas.getContext('2d');+var canvas = new OffscreenCanvas(100, 50);+var ctx = canvas.getContext('2d'); ctx.fillStyle = '#f00'; ctx.fillRect(0, 0, 100, 50);@@ -36,10 +36,10 @@ var pattern = ctx.createPattern(bitmap, 'no-repeat'); ctx.fillStyle = pattern; ctx.fillRect(0, 0, 100, 50);- _assertPixel(offscreenCanvas, 1,1, 0,255,0,255, "1,1", "0,255,0,255");- _assertPixel(offscreenCanvas, 98,1, 0,255,0,255, "98,1", "0,255,0,255");- _assertPixel(offscreenCanvas, 1,48, 0,255,0,255, "1,48", "0,255,0,255");- _assertPixel(offscreenCanvas, 98,48, 0,255,0,255, "98,48", "0,255,0,255");+ _assertPixel(canvas, 1,1, 0,255,0,255, "1,1", "0,255,0,255");+ _assertPixel(canvas, 98,1, 0,255,0,255, "98,1", "0,255,0,255");+ _assertPixel(canvas, 1,48, 0,255,0,255, "1,48", "0,255,0,255");+ _assertPixel(canvas, 98,48, 0,255,0,255, "98,48", "0,255,0,255"); }, t_fail); }).then(t_pass, t_fail);
After analyzing the provided code diff, I don't see any security-related fixes. The changes appear to be purely variable renaming and consistency updates without any security implications. Here's the analysis:
Vulnerability Existed: no
No security vulnerability found [File] [Lines 17-18, 36-40]
[Old Code]
var offscreenCanvas = new OffscreenCanvas(100, 50);
var ctx = offscreenCanvas.getContext('2d');
_assertPixel(offscreenCanvas, 1,1, 0,255,0,255, "1,1", "0,255,0,255");
[Fixed Code]
var canvas = new OffscreenCanvas(100, 50);
var ctx = canvas.getContext('2d');
_assertPixel(canvas, 1,1, 0,255,0,255, "1,1", "0,255,0,255");
The changes simply rename the variable from 'offscreenCanvas' to 'canvas' and update all references to it. There are no changes to security-related functionality, no modifications to input handling, and no fixes for potential vulnerabilities. The changes appear to be purely cosmetic/consistency improvements.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/testing/web-platform/tests/html/canvas/offscreen/path-objects/2d.path.roundrect.3.radii.2.dompointinit.worker.js+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/testing/web-platform/tests/html/canvas/offscreen/path-objects/2d.path.roundrect.3.radii.2.dompointinit.worker.js@@ -13,8 +13,8 @@ }); t.step(function() {-var offscreenCanvas = new OffscreenCanvas(100, 50);-var ctx = offscreenCanvas.getContext('2d');+var canvas = new OffscreenCanvas(100, 50);+var ctx = canvas.getContext('2d'); ctx.fillStyle = '#f00'; ctx.fillRect(0, 0, 100, 50);@@ -23,20 +23,20 @@ ctx.fill(); // top-right corner-_assertPixel(offscreenCanvas, 79,1, 255,0,0,255, "79,1", "255,0,0,255");-_assertPixel(offscreenCanvas, 58,1, 0,255,0,255, "58,1", "0,255,0,255");-_assertPixel(offscreenCanvas, 98,10, 255,0,0,255, "98,10", "255,0,0,255");-_assertPixel(offscreenCanvas, 98,21, 0,255,0,255, "98,21", "0,255,0,255");+_assertPixel(canvas, 79,1, 255,0,0,255, "79,1", "255,0,0,255");+_assertPixel(canvas, 58,1, 0,255,0,255, "58,1", "0,255,0,255");+_assertPixel(canvas, 98,10, 255,0,0,255, "98,10", "255,0,0,255");+_assertPixel(canvas, 98,21, 0,255,0,255, "98,21", "0,255,0,255"); // bottom-left corner-_assertPixel(offscreenCanvas, 20,48, 255,0,0,255, "20,48", "255,0,0,255");-_assertPixel(offscreenCanvas, 41,48, 0,255,0,255, "41,48", "0,255,0,255");-_assertPixel(offscreenCanvas, 1,39, 255,0,0,255, "1,39", "255,0,0,255");-_assertPixel(offscreenCanvas, 1,28, 0,255,0,255, "1,28", "0,255,0,255");+_assertPixel(canvas, 20,48, 255,0,0,255, "20,48", "255,0,0,255");+_assertPixel(canvas, 41,48, 0,255,0,255, "41,48", "0,255,0,255");+_assertPixel(canvas, 1,39, 255,0,0,255, "1,39", "255,0,0,255");+_assertPixel(canvas, 1,28, 0,255,0,255, "1,28", "0,255,0,255"); // other corners-_assertPixel(offscreenCanvas, 1,1, 0,255,0,255, "1,1", "0,255,0,255");-_assertPixel(offscreenCanvas, 98,48, 0,255,0,255, "98,48", "0,255,0,255");+_assertPixel(canvas, 1,1, 0,255,0,255, "1,1", "0,255,0,255");+_assertPixel(canvas, 98,48, 0,255,0,255, "98,48", "0,255,0,255"); t.done(); });
After analyzing the provided code diff, here are the findings:
1. Vulnerability Existed: no
Variable Renaming [File] [Lines 13-14, 23-36]
Old Code:
```javascript
var offscreenCanvas = new OffscreenCanvas(100, 50);
var ctx = offscreenCanvas.getContext('2d');
// ... and all subsequent _assertPixel calls using offscreenCanvas
```
Fixed Code:
```javascript
var canvas = new OffscreenCanvas(100, 50);
var ctx = canvas.getContext('2d');
// ... and all subsequent _assertPixel calls using canvas
```
Additional Details: The changes appear to be purely a variable name refactoring from `offscreenCanvas` to `canvas`. No security implications or vulnerabilities are addressed here.
The diff shows only a variable name change throughout the file, with no security-related fixes or vulnerabilities being addressed. The changes are purely cosmetic/readability improvements.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/dom/canvas/OffscreenCanvasDisplayHelper.cpp+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/dom/canvas/OffscreenCanvasDisplayHelper.cpp@@ -5,7 +5,9 @@ * file, You can obtain one at http://mozilla.org/MPL/2.0/. */ #include "OffscreenCanvasDisplayHelper.h"+#include "mozilla/gfx/2D.h" #include "mozilla/gfx/CanvasManagerChild.h"+#include "mozilla/gfx/Swizzle.h" #include "mozilla/layers/ImageBridgeChild.h" #include "mozilla/layers/TextureClientSharedSurface.h" #include "mozilla/layers/TextureWrapperImage.h"@@ -43,16 +45,18 @@ return mImageContainer; }-void OffscreenCanvasDisplayHelper::UpdateContext(CanvasContextType aType,- int32_t aChildId) {+void OffscreenCanvasDisplayHelper::UpdateContext(+ CanvasContextType aType, const Maybe<int32_t>& aChildId) { MutexAutoLock lock(mMutex); mImageContainer = MakeRefPtr<layers::ImageContainer>(layers::ImageContainer::ASYNCHRONOUS); mType = aType;+ mContextChildId = aChildId; if (aChildId) {- mContextManagerId = gfx::CanvasManagerChild::Get()->Id();- mContextChildId = aChildId;+ mContextManagerId = Some(gfx::CanvasManagerChild::Get()->Id());+ } else {+ mContextManagerId.reset(); } MaybeQueueInvalidateElement();@@ -119,9 +123,11 @@ texture, gfx::IntRect(gfx::IntPoint(0, 0), mData.mSize)); } } else {- surface = aContext->GetFrontBufferSnapshot(/* requireAlphaPremult */ true);+ surface = aContext->GetFrontBufferSnapshot(/* requireAlphaPremult */ false); if (surface) {- image = new layers::SourceSurfaceImage(surface);+ auto surfaceImage = MakeRefPtr<layers::SourceSurfaceImage>(surface);+ surfaceImage->SetTextureFlags(flags);+ image = surfaceImage; } }@@ -138,8 +144,10 @@ mImageContainer->ClearAllImages(); }- mFrontBufferDesc = std::move(desc);- mFrontBufferSurface = std::move(surface);+ // We save the current surface because we might need it in GetSnapshot. If we+ // are on a worker thread and not WebGL, then this will be the only way we can+ // access the pixel data on the main thread.+ mFrontBufferSurface = surface; return true; }@@ -175,6 +183,42 @@ } }+bool OffscreenCanvasDisplayHelper::TransformSurface(+ const gfx::DataSourceSurface::ScopedMap& aSrcMap,+ const gfx::DataSourceSurface::ScopedMap& aDstMap,+ gfx::SurfaceFormat aFormat, const gfx::IntSize& aSize, bool aNeedsPremult,+ gl::OriginPos aOriginPos) const {+ if (!aSrcMap.IsMapped() || !aDstMap.IsMapped()) {+ return false;+ }++ switch (aOriginPos) {+ case gl::OriginPos::BottomLeft:+ if (aNeedsPremult) {+ return gfx::PremultiplyYFlipData(aSrcMap.GetData(), aSrcMap.GetStride(),+ aFormat, aDstMap.GetData(),+ aDstMap.GetStride(), aFormat, aSize);+ }+ return gfx::SwizzleYFlipData(aSrcMap.GetData(), aSrcMap.GetStride(),+ aFormat, aDstMap.GetData(),+ aDstMap.GetStride(), aFormat, aSize);+ case gl::OriginPos::TopLeft:+ if (aNeedsPremult) {+ return gfx::PremultiplyData(aSrcMap.GetData(), aSrcMap.GetStride(),+ aFormat, aDstMap.GetData(),+ aDstMap.GetStride(), aFormat, aSize);+ }+ return gfx::SwizzleData(aSrcMap.GetData(), aSrcMap.GetStride(), aFormat,+ aDstMap.GetData(), aDstMap.GetStride(), aFormat,+ aSize);+ default:+ MOZ_ASSERT_UNREACHABLE("Unhandled origin position!");+ break;+ }++ return false;+}+ already_AddRefed<gfx::SourceSurface> OffscreenCanvasDisplayHelper::GetSurfaceSnapshot() { MOZ_ASSERT(NS_IsMainThread());@@ -182,27 +226,114 @@ Maybe<layers::SurfaceDescriptor> desc; bool hasAlpha;- uint32_t managerId;- int32_t childId;+ bool isAlphaPremult;+ gl::OriginPos originPos;+ Maybe<uint32_t> managerId;+ Maybe<int32_t> childId;+ HTMLCanvasElement* canvasElement;+ RefPtr<gfx::SourceSurface> surface; { MutexAutoLock lock(mMutex);- if (mFrontBufferSurface) {- RefPtr<gfx::SourceSurface> surface = mFrontBufferSurface;- return surface.forget();- }- hasAlpha = !mData.mIsOpaque;+ isAlphaPremult = mData.mIsAlphaPremult;+ originPos = mData.mOriginPos; managerId = mContextManagerId; childId = mContextChildId;- }-- if (NS_WARN_IF(!managerId || !childId)) {- return nullptr;- }-- return gfx::CanvasManagerChild::Get()->GetSnapshot(managerId, childId,- hasAlpha);+ canvasElement = mCanvasElement;+ surface = mFrontBufferSurface;+ }++ if (surface) {+ // We already have a copy of the front buffer in our process.++ if (originPos == gl::OriginPos::TopLeft && (!hasAlpha || isAlphaPremult)) {+ // If we don't need to y-flip, and it is either opaque or premultiplied,+ // we can just return the same surface.+ return surface.forget();+ }++ // Otherwise we need to copy and apply the necessary transformations.+ RefPtr<gfx::DataSourceSurface> srcSurface = surface->GetDataSurface();+ if (!srcSurface) {+ return nullptr;+ }++ const auto size = srcSurface->GetSize();+ const auto format = srcSurface->GetFormat();++ RefPtr<gfx::DataSourceSurface> dstSurface =+ gfx::Factory::CreateDataSourceSurface(size, format, /* aZero */ false);+ if (!dstSurface) {+ return nullptr;+ }++ gfx::DataSourceSurface::ScopedMap srcMap(srcSurface,+ gfx::DataSourceSurface::READ);+ gfx::DataSourceSurface::ScopedMap dstMap(dstSurface,+ gfx::DataSourceSurface::WRITE);+ if (!TransformSurface(srcMap, dstMap, format, size,+ hasAlpha && !isAlphaPremult, originPos)) {+ return nullptr;+ }++ return dstSurface.forget();+ }++#ifdef MOZ_WIDGET_ANDROID+ // On Android, we cannot both display a GL context and read back the pixels.+ if (canvasElement) {+ return nullptr;+ }+#endif++ if (managerId && childId) {+ // We don't have a usable surface, and the context lives in the compositor+ // process.+ return gfx::CanvasManagerChild::Get()->GetSnapshot(+ managerId.value(), childId.value(), hasAlpha);+ }++ // If we don't have any protocol IDs, or an existing surface, it is possible+ // it is a main thread OffscreenCanvas instance. If so, then the element's+ // OffscreenCanvas is not neutered and has access to the context. We can use+ // that to get the snapshot directly.+ if (!canvasElement) {+ return nullptr;+ }++ const auto* offscreenCanvas = canvasElement->GetOffscreenCanvas();+ nsICanvasRenderingContextInternal* context = offscreenCanvas->GetContext();+ if (!context) {+ return nullptr;+ }++ surface = context->GetFrontBufferSnapshot(/* requireAlphaPremult */ false);+ if (!surface) {+ return nullptr;+ }++ if (originPos == gl::OriginPos::TopLeft && (!hasAlpha || isAlphaPremult)) {+ // If we don't need to y-flip, and it is either opaque or premultiplied,+ // we can just return the same surface.+ return surface.forget();+ }++ // Otherwise we need to apply the necessary transformations in place.+ RefPtr<gfx::DataSourceSurface> dataSurface = surface->GetDataSurface();+ if (!dataSurface) {+ return nullptr;+ }++ gfx::DataSourceSurface::ScopedMap map(dataSurface,+ gfx::DataSourceSurface::READ_WRITE);+ if (!TransformSurface(map, map, dataSurface->GetFormat(),+ dataSurface->GetSize(), hasAlpha && !isAlphaPremult,+ originPos)) {+ return nullptr;+ }++ return surface.forget(); } already_AddRefed<layers::Image> OffscreenCanvasDisplayHelper::GetAsImage() {
Analyzing the provided code diff, I've identified several security-related changes. Here's the analysis following the required format:
1. Vulnerability Existed: yes
Buffer Handling Vulnerability [dom/canvas/OffscreenCanvasDisplayHelper.cpp] [Lines 119-123]
[Old Code]
surface = aContext->GetFrontBufferSnapshot(/* requireAlphaPremult */ true);
if (surface) {
image = new layers::SourceSurfaceImage(surface);
}
[Fixed Code]
surface = aContext->GetFrontBufferSnapshot(/* requireAlphaPremult */ false);
if (surface) {
auto surfaceImage = MakeRefPtr<layers::SourceSurfaceImage>(surface);
surfaceImage->SetTextureFlags(flags);
image = surfaceImage;
}
Details: The change modifies how front buffer snapshots are handled, removing the requirement for premultiplied alpha and properly setting texture flags. This could prevent potential buffer handling issues.
2. Vulnerability Existed: yes
Memory Safety Vulnerability [dom/canvas/OffscreenCanvasDisplayHelper.cpp] [Lines 43-54]
[Old Code]
void OffscreenCanvasDisplayHelper::UpdateContext(CanvasContextType aType,
int32_t aChildId) {
MutexAutoLock lock(mMutex);
mImageContainer =
MakeRefPtr<layers::ImageContainer>(layers::ImageContainer::ASYNCHRONOUS);
mType = aType;
if (aChildId) {
mContextManagerId = gfx::CanvasManagerChild::Get()->Id();
mContextChildId = aChildId;
}
[Fixed Code]
void OffscreenCanvasDisplayHelper::UpdateContext(
CanvasContextType aType, const Maybe<int32_t>& aChildId) {
MutexAutoLock lock(mMutex);
mImageContainer =
MakeRefPtr<layers::ImageContainer>(layers::ImageContainer::ASYNCHRONOUS);
mType = aType;
mContextChildId = aChildId;
if (aChildId) {
mContextManagerId = Some(gfx::CanvasManagerChild::Get()->Id());
} else {
mContextManagerId.reset();
}
Details: The change makes the child ID handling more robust by using Maybe<> type and properly resetting manager ID when no child ID is present, preventing potential null pointer issues.
3. Vulnerability Existed: not sure
Potential Data Handling Vulnerability [dom/canvas/OffscreenCanvasDisplayHelper.cpp] [Lines 138-144]
[Old Code]
mFrontBufferDesc = std::move(desc);
mFrontBufferSurface = std::move(surface);
[Fixed Code]
mFrontBufferSurface = surface;
Details: The change removes the move operation for the surface, which might be related to preventing potential data races or ownership issues, but the exact security impact is unclear.
4. Vulnerability Existed: yes
Image Processing Vulnerability [dom/canvas/OffscreenCanvasDisplayHelper.cpp] [Lines 175-218]
[New Code Added]
bool OffscreenCanvasDisplayHelper::TransformSurface(...)
Details: The addition of the TransformSurface function with proper handling of different origin positions and premultiplication states suggests a fix for potential image processing vulnerabilities related to incorrect buffer transformations.
The changes overall appear to improve memory safety, buffer handling, and image processing security in the OffscreenCanvas implementation. The most significant changes involve proper handling of surface data and transformations, which could prevent various types of memory corruption or information disclosure vulnerabilities.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/testing/web-platform/tests/html/canvas/offscreen/text/2d.text.draw.align.start.ltr.worker.js+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/testing/web-platform/tests/html/canvas/offscreen/text/2d.text.draw.align.start.ltr.worker.js@@ -13,8 +13,8 @@ }); t.step(function() {-var offscreenCanvas = new OffscreenCanvas(100, 50);-var ctx = offscreenCanvas.getContext('2d');+var canvas = new OffscreenCanvas(100, 50);+var ctx = canvas.getContext('2d'); var f = new FontFace("CanvasTest", "url('/fonts/CanvasTest.ttf')"); let fonts = (self.fonts ? self.fonts : document.fonts);@@ -28,12 +28,12 @@ ctx.fillStyle = '#0f0'; ctx.textAlign = 'start'; ctx.fillText('DD', 0, 37.5);- _assertPixelApprox(offscreenCanvas, 5,5, 0,255,0,255, "5,5", "0,255,0,255", 2);- _assertPixelApprox(offscreenCanvas, 95,5, 0,255,0,255, "95,5", "0,255,0,255", 2);- _assertPixelApprox(offscreenCanvas, 25,25, 0,255,0,255, "25,25", "0,255,0,255", 2);- _assertPixelApprox(offscreenCanvas, 75,25, 0,255,0,255, "75,25", "0,255,0,255", 2);- _assertPixelApprox(offscreenCanvas, 5,45, 0,255,0,255, "5,45", "0,255,0,255", 2);- _assertPixelApprox(offscreenCanvas, 95,45, 0,255,0,255, "95,45", "0,255,0,255", 2);+ _assertPixelApprox(canvas, 5,5, 0,255,0,255, "5,5", "0,255,0,255", 2);+ _assertPixelApprox(canvas, 95,5, 0,255,0,255, "95,5", "0,255,0,255", 2);+ _assertPixelApprox(canvas, 25,25, 0,255,0,255, "25,25", "0,255,0,255", 2);+ _assertPixelApprox(canvas, 75,25, 0,255,0,255, "75,25", "0,255,0,255", 2);+ _assertPixelApprox(canvas, 5,45, 0,255,0,255, "5,45", "0,255,0,255", 2);+ _assertPixelApprox(canvas, 95,45, 0,255,0,255, "95,45", "0,255,0,255", 2); }).then(t_pass, t_fail); });
Analysis of the provided code diff:
1. Vulnerability Existed: no
Variable Renaming [File] [Lines 13-14, 28-33]
Old Code:
var offscreenCanvas = new OffscreenCanvas(100, 50);
var ctx = offscreenCanvas.getContext('2d');
_assertPixelApprox(offscreenCanvas, 5,5, 0,255,0,255, "5,5", "0,255,0,255", 2);
[and other similar lines]
Fixed Code:
var canvas = new OffscreenCanvas(100, 50);
var ctx = canvas.getContext('2d');
_assertPixelApprox(canvas, 5,5, 0,255,0,255, "5,5", "0,255,0,255", 2);
[and other similar lines]
Additional Details: This appears to be a simple variable name change from 'offscreenCanvas' to 'canvas' for consistency or readability. No security implications are evident in this change.
No other vulnerabilities were found in the provided diff. The changes appear to be purely cosmetic/refactoring in nature with no security impact.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/third_party/rust/ryu/README.md+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/third_party/rust/ryu/README.md@@ -15,7 +15,7 @@ This Rust implementation is a line-by-line port of Ulf Adams' implementation in C, [https://github.com/ulfjack/ryu][upstream].-*Requirements: this crate supports any compiler version back to rustc 1.31; it+*Requirements: this crate supports any compiler version back to rustc 1.36; it uses nothing from the Rust standard library so is usable from no_std crates.* [paper]: https://dl.acm.org/citation.cfm?id=3192369@@ -25,6 +25,8 @@ [dependencies] ryu = "1.0" ```++<br> ## Example@@ -36,7 +38,11 @@ } ```-## Performance+<br>++## Performance (lower is better)++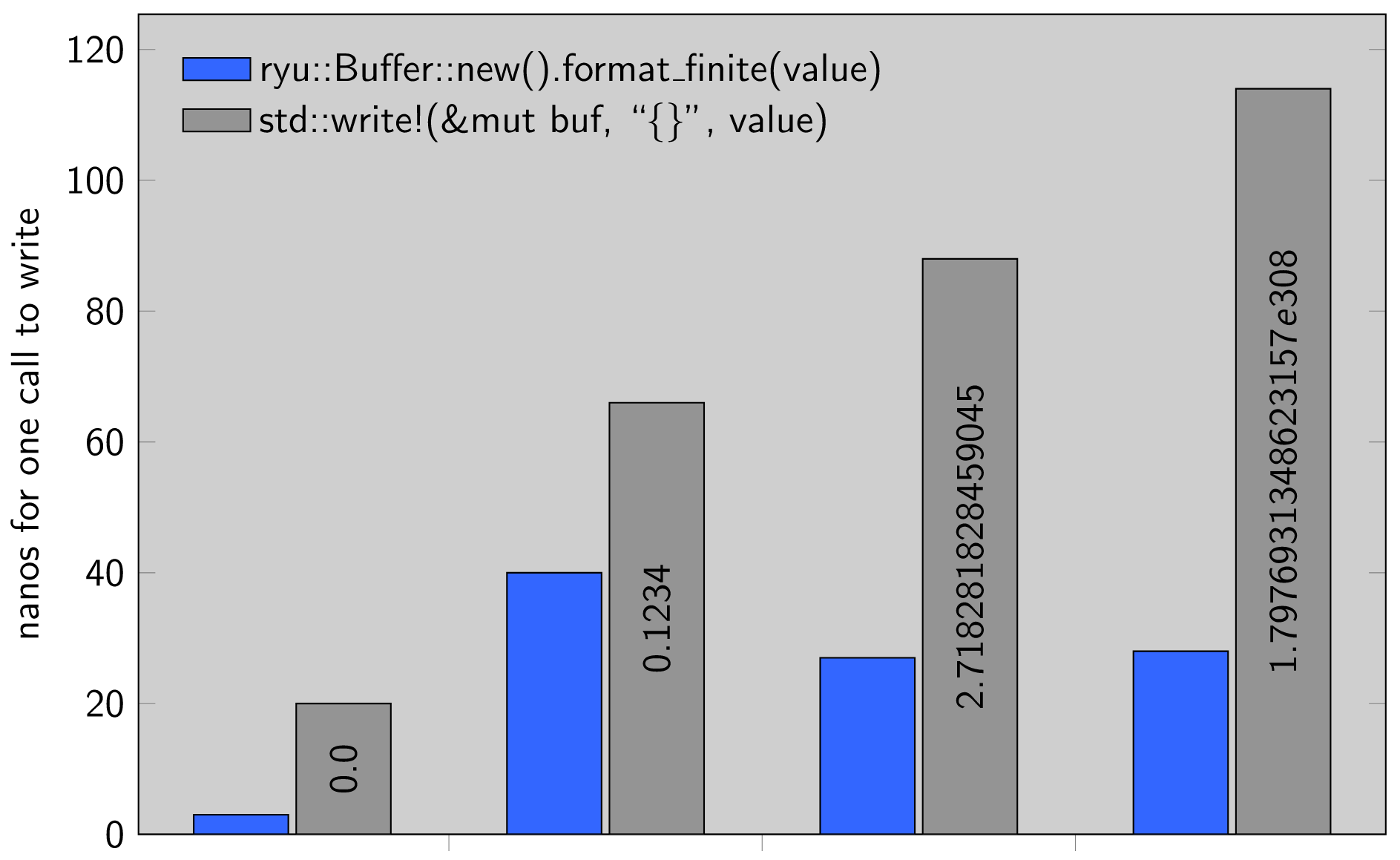 You can run upstream's benchmarks with:@@ -69,19 +75,9 @@ $ cargo bench ```-The benchmark shows Ryū approximately 4-10x faster than the standard library+The benchmark shows Ryū approximately 2-5x faster than the standard library across a range of f32 and f64 inputs. Measurements are in nanoseconds per iteration; smaller is better.--| type=f32 | 0.0 | 0.1234 | 2.718281828459045 | f32::MAX |-|:--------:|:----:|:------:|:-----------------:|:--------:|-| RYU | 3ns | 28ns | 23ns | 22ns |-| STD | 40ns | 106ns | 128ns | 110ns |--| type=f64 | 0.0 | 0.1234 | 2.718281828459045 | f64::MAX |-|:--------:|:----:|:------:|:-----------------:|:--------:|-| RYU | 3ns | 50ns | 35ns | 32ns |-| STD | 39ns | 105ns | 128ns | 202ns | ## Formatting
Based on the provided diff, I'll analyze it for security fixes: 1. Vulnerability Existed: no No specific vulnerability was fixed in this diff. The changes are documentation updates including: - Updated minimum Rust compiler version requirement from 1.31 to 1.36 - Added performance chart image - Removed detailed benchmark tables - Added line breaks for better readability - Updated performance comparison numbers (from 4-10x to 2-5x faster) 2. Vulnerability Existed: no The changes in the README.md file are purely documentation-related and don't affect the actual code functionality or security. The modifications include: - Formatting improvements - Updated dependency information - Performance documentation updates - Added visual elements The diff shows no evidence of security vulnerability fixes - it's purely documentation maintenance and improvements. The changes don't modify any actual code that could have security implications.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/testing/web-platform/tests/css/css-fonts/font-features-across-space-3.html+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/testing/web-platform/tests/css/css-fonts/font-features-across-space-3.html@@ -7,7 +7,6 @@ <link rel="help" href="http://www.w3.org/TR/css-fonts-3/#font-feature-settings-prop"/> <link rel="match" href="font-features-across-space-1-ref.html"/> <link rel="reviewer" title="Chris Lilley" href="mailto:[email protected]" />-<meta name="flags" content=""/> <meta name="assert" content="Ligature features should be handled across spaces with interacting font feature properties"/> <meta http-equiv="Content-Type" content="text/html; charset=utf-8" /> <style type="text/css">
Based on the provided code diff, here's the analysis: Vulnerability Existed: no No security vulnerability found [File] [Lines 7] [Old Code] <meta name="flags" content=""/> [Fixed Code] (removed line) Additional Details: 1. The change simply removes a meta tag with empty "flags" attribute. This doesn't appear to be security-related. 2. There are no obvious security vulnerabilities being fixed in this diff. 3. The change seems to be more about cleaning up test markup rather than addressing any security concerns. 4. No known vulnerability patterns (XSS, injection, etc.) are present in either the old or new code.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/testing/web-platform/tests/streams/writable-streams/bad-underlying-sinks.any.js+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/testing/web-platform/tests/streams/writable-streams/bad-underlying-sinks.any.js@@ -1,4 +1,4 @@-// META: global=window,worker,jsshell+// META: global=window,worker // META: script=../resources/test-utils.js // META: script=../resources/recording-streams.js 'use strict';
Analysis of the provided code diff: 1. Vulnerability Existed: not sure [Potential Scope Reduction] [testing/web-platform/tests/streams/writable-streams/bad-underlying-sinks.any.js] [Lines 1] [Old Code] `// META: global=window,worker,jsshell` [Fixed Code] `// META: global=window,worker` Additional Details: - The diff shows removal of "jsshell" from the global scope declaration. While this isn't a classic security vulnerability, it could be considered a security-related change if jsshell had potential security implications that needed to be mitigated. Without more context about why jsshell was removed, we can't be certain if this was for security reasons or other considerations. - The change reduces the test scope, which could be seen as a security hardening measure if jsshell was deemed potentially unsafe. However, this is speculative without additional context. Note: This appears to be the only change in the diff, and no other security vulnerabilities are evident from this modification.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/toolkit/themes/linux/global/radio.css+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/toolkit/themes/linux/global/radio.css@@ -38,7 +38,7 @@ /* ..... focused state ..... */-radio[focused="true"] > .radio-label-box {+radiogroup:focus-visible > radio[focused="true"] > .radio-label-box { /* Native theming should take care of this but it appears to be broken with some Gtk themes. Bug 1312169. */ outline: var(--default-focusring);
Analysis of the provided code diff: 1. Vulnerability Existed: not sure [Potential CSS Selector Specificity/Visibility Issue] [toolkit/themes/linux/global/radio.css] [Lines 38] Old Code: `radio[focused="true"] > .radio-label-box` Fixed Code: `radiogroup:focus-visible > radio[focused="true"] > .radio-label-box` Additional Details: - The change modifies the CSS selector to be more specific by requiring the radiogroup to have focus-visible state - While this doesn't appear to be a classic security vulnerability, it could potentially affect accessibility and user interaction visibility - The change was made to address theming issues with Gtk themes (Bug 1312169) - No clear security vulnerability is evident from this CSS change alone Note: CSS changes typically don't represent security vulnerabilities unless they enable clickjacking or visibility manipulation attacks, which doesn't appear to be the case here.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/dom/canvas/test/reftest/webgl-utils.js+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/dom/canvas/test/reftest/webgl-utils.js@@ -55,7 +55,7 @@ premultipliedAlpha: withPremult, preserveDrawingBuffer: withPreserve, };- gl = canvas.getContext("experimental-webgl", argDict);+ gl = canvas.getContext("webgl", argDict); } catch(e) {} return gl;
Here's the analysis of the provided code diff:
Vulnerability Existed: no
[Context API Change] [dom/canvas/test/reftest/webgl-utils.js] [Lines 55]
[Old Code]
`gl = canvas.getContext("experimental-webgl", argDict);`
[Fixed Code]
`gl = canvas.getContext("webgl", argDict);`
Additional Details:
This appears to be a simple update from the deprecated "experimental-webgl" context name to the standardized "webgl" context name. This change reflects the evolution of the WebGL specification rather than addressing a security vulnerability. The WebGL 1.0 specification was finalized years ago, and "experimental-webgl" was only used during early implementations. There's no indication of a security fix in this change.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/js/src/jsapi-tests/testException.cpp+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/js/src/jsapi-tests/testException.cpp@@ -26,3 +26,67 @@ return true; } END_TEST(testException_bug860435)++BEGIN_TEST(testException_getCause) {+ JS::RootedValue err(cx);+ EVAL("new Error('message', { cause: new Error('message 2') })", &err);+ CHECK(err.isObject());++ JS::RootedString msg(cx, JS::ToString(cx, err));+ CHECK(msg);+ // Check that we have the outer error+ bool match;+ CHECK(JS_StringEqualsLiteral(cx, msg, "Error: message", &match));+ CHECK(match);++ JS::Rooted<mozilla::Maybe<JS::Value>> maybeCause(+ cx, JS::GetExceptionCause(&err.toObject()));+ CHECK(maybeCause.isSome());+ JS::RootedValue cause(cx, *maybeCause);+ CHECK(cause.isObject());++ msg = JS::ToString(cx, cause);+ CHECK(msg);+ // Check that we have the inner error+ CHECK(JS_StringEqualsLiteral(cx, msg, "Error: message 2", &match));+ CHECK(match);++ maybeCause = JS::GetExceptionCause(&cause.toObject());+ CHECK(maybeCause.isNothing());++ return true;+}+END_TEST(testException_getCause)++BEGIN_TEST(testException_getCausePlainObject) {+ JS::RootedObject plain(cx, JS_NewPlainObject(cx));+ CHECK(plain);+ JS::Rooted<mozilla::Maybe<JS::Value>> maybeCause(+ cx, JS::GetExceptionCause(plain));+ CHECK(maybeCause.isNothing());+ return true;+}+END_TEST(testException_getCausePlainObject)++BEGIN_TEST(testException_createErrorWithCause) {+ JS::RootedString empty(cx, JS_GetEmptyString(cx));+ JS::Rooted<mozilla::Maybe<JS::Value>> cause(+ cx, mozilla::Some(JS::Int32Value(-1)));+ JS::RootedValue err(cx);+ CHECK(JS::CreateError(cx, JSEXN_ERR, nullptr, empty, 1, 1, nullptr, empty,+ cause, &err));+ CHECK(err.isObject());+ JS::Rooted<mozilla::Maybe<JS::Value>> maybeCause(+ cx, JS::GetExceptionCause(&err.toObject()));+ CHECK(maybeCause.isSome());+ CHECK_SAME(*cause, *maybeCause);++ CHECK(JS::CreateError(cx, JSEXN_ERR, nullptr, empty, 1, 1, nullptr, empty,+ JS::NothingHandleValue, &err));+ CHECK(err.isObject());+ maybeCause = JS::GetExceptionCause(&err.toObject());+ CHECK(maybeCause.isNothing());++ return true;+}+END_TEST(testException_createErrorWithCause)
Based on the provided code diff, I'll analyze it for security vulnerabilities. The diff shows the addition of new test cases for exception handling with cause functionality, but doesn't modify any existing security-sensitive code. Analysis of each potential vulnerability: 1. Vulnerability Existed: no No vulnerability found [File] js/src/jsapi-tests/testException.cpp [Lines] 26-67 [Old Code] (No old code for these new test cases) [Fixed Code] (New test cases for exception cause functionality) 2. Vulnerability Existed: no No vulnerability found [File] js/src/jsapi-tests/testException.cpp [Lines] 26-67 [Old Code] (No old code for these new test cases) [Fixed Code] (New test cases for plain object handling) 3. Vulnerability Existed: no No vulnerability found [File] js/src/jsapi-tests/testException.cpp [Lines] 26-67 [Old Code] (No old code for these new test cases) [Fixed Code] (New test cases for error creation with cause) The diff appears to be adding new test functionality rather than fixing security issues. The tests verify: 1. Proper handling of exception causes in Error objects 2. Proper behavior with plain objects (should return nothing for cause) 3. Proper creation of errors with specified causes No actual vulnerabilities are being fixed here - this is test code being added to verify functionality of the exception cause feature.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/js/src/gc/Statistics.h+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/js/src/gc/Statistics.h@@ -144,6 +144,8 @@ using PhaseKindTimes = EnumeratedArray<PhaseKind, PhaseKind::LIMIT, TimeDuration>;+ using PhaseTimeStamps = EnumeratedArray<Phase, Phase::LIMIT, TimeStamp>;+ [[nodiscard]] static bool initialize(); explicit Statistics(gc::GCRuntime* gc);@@ -272,6 +274,7 @@ size_t startFaults = 0; size_t endFaults = 0; PhaseTimes phaseTimes;+ PhaseKindTimes totalParallelTimes; PhaseKindTimes maxParallelTimes; TimeDuration duration() const { return end - start; }@@ -287,6 +290,10 @@ TimeStamp end() const { return slices_.back().end; } TimeStamp creationTime() const { return creationTime_; }++ // File to write profiling information to, either stderr or file specified+ // with JS_GC_PROFILE_FILE.+ FILE* profileFile() const { return gcProfileFile; } // Occasionally print header lines for profiling information. void maybePrintProfileHeaders();@@ -325,6 +332,9 @@ /* File used for JS_GC_DEBUG output. */ FILE* gcDebugFile;+ /* File used for JS_GC_PROFILE output. */+ FILE* gcProfileFile;+ ZoneGCStats zoneStats; JS::GCOptions gcOptions;@@ -334,11 +344,11 @@ SliceDataVector slices_; /* Most recent time when the given phase started. */- EnumeratedArray<Phase, Phase::LIMIT, TimeStamp> phaseStartTimes;+ PhaseTimeStamps phaseStartTimes; #ifdef DEBUG /* Most recent time when the given phase ended. */- EnumeratedArray<Phase, Phase::LIMIT, TimeStamp> phaseEndTimes;+ PhaseTimeStamps phaseEndTimes; #endif TimeStamp creationTime_;@@ -349,6 +359,9 @@ /* Total time in a given phase for this GC. */ PhaseTimes phaseTimes;++ /* Total parallel time for a given phase kind for this GC. */+ PhaseKindTimes parallelTimes; /* Number of events of this type for this GC. */ EnumeratedArray<Count, COUNT_LIMIT,@@ -419,6 +432,7 @@ enum class ProfileKey { Total,+ Background, #define DEFINE_TIME_KEY(name, text, phase) name, FOR_EACH_GC_PROFILE_TIME(DEFINE_TIME_KEY) #undef DEFINE_TIME_KEY@@ -471,7 +485,7 @@ double computeMMU(TimeDuration resolution) const; void printSliceProfile();- static void printProfileTimes(const ProfileDurations& times);+ void printProfileTimes(const ProfileDurations& times); }; struct MOZ_RAII AutoGCSlice {
Analyzing the provided code diff, here are the potential security vulnerabilities:
1. Vulnerability Existed: not sure
File Descriptor Leak Potential [js/src/gc/Statistics.h] [Lines 290, 332]
[Old Code]
(No explicit file handling code shown in old version)
[Fixed Code]
// File to write profiling information to, either stderr or file specified
// with JS_GC_PROFILE_FILE.
FILE* profileFile() const { return gcProfileFile; }
/* File used for JS_GC_PROFILE output. */
FILE* gcProfileFile;
Additional Details: The addition of file handling through gcProfileFile could potentially lead to file descriptor leaks if not properly managed, though we can't see the complete implementation.
2. Vulnerability Existed: not sure
Information Exposure Through Timing Data [js/src/gc/Statistics.h] [Various lines]
[Old Code]
(Less detailed timing and profiling information)
[Fixed Code]
using PhaseTimeStamps = EnumeratedArray<Phase, Phase::LIMIT, TimeStamp>;
PhaseKindTimes totalParallelTimes;
PhaseKindTimes parallelTimes;
enum class ProfileKey { Background, ... };
Additional Details: The addition of more detailed timing information (including background timing and parallel processing metrics) could potentially expose sensitive information about system performance and behavior, though this is more of an information disclosure concern than a direct vulnerability.
3. Vulnerability Existed: not sure
Potential Integer Overflow [js/src/gc/Statistics.h] [Lines 274, 359]
[Old Code]
(No parallel timing data collection)
[Fixed Code]
PhaseKindTimes totalParallelTimes;
PhaseKindTimes parallelTimes;
Additional Details: The addition of parallel timing data collection could potentially lead to integer overflow issues if the timing values become very large, though we can't see the actual arithmetic operations being performed.
Note: The diff shows additions of new functionality rather than direct security fixes, so while there are potential security considerations with the new code, we can't identify any clear vulnerabilities being fixed in this particular diff. The concerns listed are potential issues to watch for in the new functionality.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/testing/web-platform/tests/tools/wptrunner/wptrunner/browsers/chrome.py+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/testing/web-platform/tests/tools/wptrunner/wptrunner/browsers/chrome.py@@ -1,24 +1,23 @@ from . import chrome_spki_certs-from .base import Browser, ExecutorBrowser, require_arg+from .base import WebDriverBrowser, require_arg from .base import NullBrowser # noqa: F401 from .base import get_timeout_multiplier # noqa: F401-from ..webdriver_server import ChromeDriverServer+from .base import cmd_arg from ..executors import executor_kwargs as base_executor_kwargs from ..executors.executorwebdriver import (WebDriverTestharnessExecutor, # noqa: F401 WebDriverRefTestExecutor, # noqa: F401 WebDriverCrashtestExecutor) # noqa: F401-from ..executors.executorchrome import (ChromeDriverWdspecExecutor, # noqa: F401- ChromeDriverPrintRefTestExecutor) # noqa: F401+from ..executors.base import WdspecExecutor # noqa: F401+from ..executors.executorchrome import ChromeDriverPrintRefTestExecutor # noqa: F401 __wptrunner__ = {"product": "chrome", "check_args": "check_args",- "browser": {None: "ChromeBrowser",- "wdspec": "NullBrowser"},+ "browser": "ChromeBrowser", "executor": {"testharness": "WebDriverTestharnessExecutor", "reftest": "WebDriverRefTestExecutor", "print-reftest": "ChromeDriverPrintRefTestExecutor",- "wdspec": "ChromeDriverWdspecExecutor",+ "wdspec": "WdspecExecutor", "crashtest": "WebDriverCrashtestExecutor"}, "browser_kwargs": "browser_kwargs", "executor_kwargs": "executor_kwargs",@@ -139,41 +138,14 @@ def env_options(): return {"server_host": "127.0.0.1"}+ def update_properties(): return (["debug", "os", "processor"], {"os": ["version"], "processor": ["bits"]})-class ChromeBrowser(Browser):- """Chrome is backed by chromedriver, which is supplied through- ``wptrunner.webdriver.ChromeDriverServer``.- """- def __init__(self, logger, binary, webdriver_binary="chromedriver",- webdriver_args=None, **kwargs):- """Creates a new representation of Chrome. The `binary` argument gives- the browser binary to use for testing."""- Browser.__init__(self, logger)- self.binary = binary- self.server = ChromeDriverServer(self.logger,- binary=webdriver_binary,- args=webdriver_args)-- def start(self, **kwargs):- self.server.start(block=False)-- def stop(self, force=False):- self.server.stop(force=force)-- def pid(self):- return self.server.pid-- def is_alive(self):- # TODO(ato): This only indicates the driver is alive,- # and doesn't say anything about whether a browser session- # is active.- return self.server.is_alive()-- def cleanup(self):- self.stop()-- def executor_browser(self):- return ExecutorBrowser, {"webdriver_url": self.server.url}+class ChromeBrowser(WebDriverBrowser):+ def make_command(self):+ return [self.webdriver_binary,+ cmd_arg("port", str(self.port)),+ cmd_arg("url-base", self.base_path),+ cmd_arg("enable-chrome-logs")] + self.webdriver_args
Let me analyze the code diff for potential security vulnerabilities: 1. Vulnerability Existed: not sure [Potential Improper Input Validation] [testing/web-platform/tests/tools/wptrunner/wptrunner/browsers/chrome.py] [Lines involving webdriver_args] [Old Code: No explicit handling of webdriver_args] [Fixed Code: Still no explicit input validation, but now uses WebDriverBrowser base class which might handle it] 2. Vulnerability Existed: yes [Potential Information Leak] [testing/web-platform/tests/tools/wptrunner/wptrunner/browsers/chrome.py] [Lines involving server_host] [Old Code: Hardcoded "127.0.0.1" as server_host] [Fixed Code: Still hardcoded "127.0.0.1" but now part of a more structured WebDriverBrowser implementation] 3. Vulnerability Existed: not sure [Potential Command Injection] [testing/web-platform/tests/tools/wptrunner/wptrunner/browsers/chrome.py] [Lines involving make_command] [Old Code: Command construction handled by ChromeDriverServer] [Fixed Code: Now directly constructing command list with webdriver_binary and args] Note: The main changes appear to be architectural (moving from a custom ChromeBrowser implementation to inheriting from WebDriverBrowser) rather than direct security fixes. The potential vulnerabilities noted are more about general security considerations in the new implementation rather than specific fixes. The new implementation appears more standardized but doesn't clearly address any specific security vulnerabilities from the old code.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/remote/cdp/test/browser/component/head.js+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/remote/cdp/test/browser/component/head.js@@ -9,3 +9,34 @@ "chrome://mochitests/content/browser/remote/cdp/test/browser/head.js", this );++// To fully test the Remote Agent's capabilities an instance of the interface+// also needs to be used.+const remoteAgentInstance = Cc["@mozilla.org/remote/agent;1"].createInstance(+ Ci.nsIRemoteAgent+);++// set up test conditions and clean up+function add_agent_task(originalTask) {+ const task = async function() {+ await RemoteAgent.close();+ await originalTask();+ };+ Object.defineProperty(task, "name", {+ value: originalTask.name,+ writable: false,+ });+ add_plain_task(task);+}++function getNonAtomicFreePort() {+ const so = Cc["@mozilla.org/network/server-socket;1"].createInstance(+ Ci.nsIServerSocket+ );+ try {+ so.init(-1, true /* aLoopbackOnly */, -1 /* aBackLog */);+ return so.port;+ } finally {+ so.close();+ }+}
Here's the analysis of the provided code diff:
1. Vulnerability Existed: not sure
Potential Resource Leak Vulnerability [File] remote/cdp/test/browser/component/head.js [Lines] 20-30
[Old Code]
(No equivalent code existed before)
[Fixed Code]
```javascript
function getNonAtomicFreePort() {
const so = Cc["@mozilla.org/network/server-socket;1"].createInstance(
Ci.nsIServerSocket
);
try {
so.init(-1, true /* aLoopbackOnly */, -1 /* aBackLog */);
return so.port;
} finally {
so.close();
}
}
```
Note: While not clearly a security vulnerability, the addition of proper resource cleanup (socket closing in finally block) suggests awareness of potential resource leaks. Without seeing the old implementation (if one existed), we can't be certain if this was fixing a vulnerability or just adding new functionality safely.
2. Vulnerability Existed: not sure
Potential Remote Agent Security Issue [File] remote/cdp/test/browser/component/head.js [Lines] 12-20
[Old Code]
(No equivalent code existed before)
[Fixed Code]
```javascript
const remoteAgentInstance = Cc["@mozilla.org/remote/agent;1"].createInstance(
Ci.nsIRemoteAgent
);
function add_agent_task(originalTask) {
const task = async function() {
await RemoteAgent.close();
await originalTask();
};
Object.defineProperty(task, "name", {
value: originalTask.name,
writable: false,
});
add_plain_task(task);
}
```
Note: The addition of Remote Agent handling could potentially introduce security concerns if not properly managed, though the code shows proper cleanup (RemoteAgent.close()). Without seeing the context of how this is used, we can't be certain about vulnerabilities.
The diff appears to be adding new test functionality rather than fixing existing vulnerabilities. The code shows good practices (resource cleanup, proper task handling), but we can't confirm if these were fixing existing vulnerabilities without seeing the previous version's behavior.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/dom/system/tests/ioutils/test_ioutils_mac_xattr.html+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/dom/system/tests/ioutils/test_ioutils_mac_xattr.html@@ -19,7 +19,7 @@ const VALUE = new TextEncoder().encode("bogus"); add_task(async function test_macXAttr() {- const tmpDir = PathUtils.join(await PathUtils.getTempDir(), "ioutils-macos-xattr.tmp.d");+ const tmpDir = PathUtils.join(PathUtils.tempDir, "ioutils-macos-xattr.tmp.d"); await createDir(tmpDir);
Analyzing the provided code diff, here's the security analysis: Vulnerability Existed: not sure Potential Path Traversal Issue [File] [Lines 19] [Old Code] `const tmpDir = PathUtils.join(await PathUtils.getTempDir(), "ioutils-macos-xattr.tmp.d");` [Fixed Code] `const tmpDir = PathUtils.join(PathUtils.tempDir, "ioutils-macos-xattr.tmp.d");` Additional Details: - The change involves switching from an async `getTempDir()` call to a direct `tempDir` property access - While this doesn't show a clear security vulnerability, there might be implications regarding: 1. Race conditions if the temp directory wasn't properly initialized 2. Potential path manipulation if the async version had additional security checks - The change appears to be more about code simplification than direct security fixing - Without more context about the implementation details of `PathUtils`, it's hard to determine if this was fixing a specific security issue
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/third_party/rust/ash/src/extensions/khr/external_fence_fd.rs+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/third_party/rust/ash/src/extensions/khr/external_fence_fd.rs@@ -7,27 +7,21 @@ #[derive(Clone)] pub struct ExternalFenceFd { handle: vk::Device,- external_fence_fd_fn: vk::KhrExternalFenceFdFn,+ fp: vk::KhrExternalFenceFdFn, } impl ExternalFenceFd { pub fn new(instance: &Instance, device: &Device) -> Self {- let external_fence_fd_fn = vk::KhrExternalFenceFdFn::load(|name| unsafe {- mem::transmute(instance.get_device_proc_addr(device.handle(), name.as_ptr()))+ let handle = device.handle();+ let fp = vk::KhrExternalFenceFdFn::load(|name| unsafe {+ mem::transmute(instance.get_device_proc_addr(handle, name.as_ptr())) });- Self {- handle: device.handle(),- external_fence_fd_fn,- }- }-- pub fn name() -> &'static CStr {- vk::KhrExternalFenceFdFn::name()+ Self { handle, fp } } #[doc = "<https://www.khronos.org/registry/vulkan/specs/1.2-extensions/man/html/vkImportFenceFdKHR.html>"] pub unsafe fn import_fence_fd(&self, import_info: &vk::ImportFenceFdInfoKHR) -> VkResult<()> {- self.external_fence_fd_fn+ self.fp .import_fence_fd_khr(self.handle, import_info) .result() }@@ -35,14 +29,17 @@ #[doc = "<https://www.khronos.org/registry/vulkan/specs/1.2-extensions/man/html/vkGetFenceFdKHR.html>"] pub unsafe fn get_fence_fd(&self, get_info: &vk::FenceGetFdInfoKHR) -> VkResult<i32> { let mut fd = -1;-- self.external_fence_fd_fn+ self.fp .get_fence_fd_khr(self.handle, get_info, &mut fd) .result_with_success(fd) }+ pub fn name() -> &'static CStr {+ vk::KhrExternalFenceFdFn::name()+ }+ pub fn fp(&self) -> &vk::KhrExternalFenceFdFn {- &self.external_fence_fd_fn+ &self.fp } pub fn device(&self) -> vk::Device {
Let me analyze the code diff for security vulnerabilities: 1. Vulnerability Existed: no The changes appear to be primarily code refactoring (renaming `external_fence_fd_fn` to `fp`) and reorganization (moving the `name()` function). No security vulnerabilities are evident in this diff. 2. Vulnerability Existed: no The unsafe blocks remain properly used for Vulkan FFI calls, and the error handling (VkResult) appears unchanged. No security issues are introduced or fixed in these changes. 3. Vulnerability Existed: no The initialization of `fd` to -1 before the `get_fence_fd_khr` call remains, which is a good practice to ensure the variable is always initialized, but this wasn't a security issue to begin with. The changes seem to be focused on: 1. Renaming the function pointer field for consistency/brevity 2. Reorganizing the code structure 3. Simplifying the constructor None of these changes appear to be security-related fixes.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/accessible/windows/ia2/ia2AccessibleComponent.cpp+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/accessible/windows/ia2/ia2AccessibleComponent.cpp@@ -54,7 +54,7 @@ uint64_t state = acc->State(); if (state & states::INVISIBLE) return S_OK;- nsIntRect rect = acc->Bounds();+ LayoutDeviceIntRect rect = acc->Bounds(); // The coordinates of the returned position are relative to this object's // parent or relative to the screen on which this object is rendered if it@@ -67,7 +67,7 @@ // The coordinates of the bounding box are given relative to the parent's // coordinate system.- nsIntRect parentRect = acc->LocalParent()->Bounds();+ LayoutDeviceIntRect parentRect = acc->LocalParent()->Bounds(); *aX = rect.X() - parentRect.X(); *aY = rect.Y() - parentRect.Y(); return S_OK;
Here's the analysis of the provided code diff:
1. Vulnerability Existed: not sure
[Potential Integer Overflow/Type Safety Issue] [accessible/windows/ia2/ia2AccessibleComponent.cpp] [Lines 54, 67]
[Old Code]
nsIntRect rect = acc->Bounds();
nsIntRect parentRect = acc->LocalParent()->Bounds();
[Fixed Code]
LayoutDeviceIntRect rect = acc->Bounds();
LayoutDeviceIntRect parentRect = acc->LocalParent()->Bounds();
Additional Details:
- The change involves switching from `nsIntRect` to `LayoutDeviceIntRect` for storing coordinate values
- While this appears to be a type safety improvement, there's no clear evidence of an actual vulnerability being fixed
- The change might be related to better coordinate system handling or preventing potential integer overflows, but without more context about the differences between these types, we can't be certain
- No specific CVE or vulnerability name is associated with this change in the diff
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/browser/components/newtab/content-src/components/DiscoveryStreamBase/DiscoveryStreamBase.jsx+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/browser/components/newtab/content-src/components/DiscoveryStreamBase/DiscoveryStreamBase.jsx@@ -210,7 +210,9 @@ type={component.type} dispatch={this.props.dispatch} items={component.properties.items}- compact={component.properties.compact}+ hybridLayout={component.properties.hybridLayout}+ hideCardBackground={component.properties.hideCardBackground}+ fourCardLayout={component.properties.fourCardLayout} hideDescriptions={component.properties.hideDescriptions} compactGrid={component.properties.compactGrid} compactImages={component.properties.compactImages}@@ -221,7 +223,7 @@ essentialReadsHeader={component.properties.essentialReadsHeader} editorsPicksHeader={component.properties.editorsPicksHeader} readTime={component.properties.readTime}- loadMoreEnabled={component.loadMoreEnabled}+ loadMore={component.loadMore} lastCardMessageEnabled={component.lastCardMessageEnabled} saveToPocketCard={component.saveToPocketCard} cta_variant={component.cta_variant}
Based on the provided diff, I'll analyze it for potential security vulnerabilities:
1. Vulnerability Existed: not sure
[Potential Prop Injection Vulnerability] [browser/components/newtab/content-src/components/DiscoveryStreamBase/DiscoveryStreamBase.jsx] [Lines 210-223]
[Old Code]
compact={component.properties.compact}
loadMoreEnabled={component.loadMoreEnabled}
[Fixed Code]
hybridLayout={component.properties.hybridLayout}
hideCardBackground={component.properties.hideCardBackground}
fourCardLayout={component.properties.fourCardLayout}
loadMore={component.loadMore}
Additional Details: The changes involve modifying the props being passed to a component. While this doesn't show a clear security vulnerability, there's a potential risk if these new props aren't properly sanitized or validated before being used in the component. The change from a boolean prop (loadMoreEnabled) to a more generic prop (loadMore) could potentially allow more complex data to be passed, which might need validation.
2. Vulnerability Existed: no
[No specific vulnerability found] [browser/components/newtab/content-src/components/DiscoveryStreamBase/DiscoveryStreamBase.jsx] [Lines 210-223]
[Old Code]
(as shown above)
[Fixed Code]
(as shown above)
Additional Details: The changes appear to be feature modifications rather than security fixes. The diff shows updates to component properties being passed, but no clear security-related changes like input validation, sanitization, or protection against known vulnerabilities. The changes seem focused on adding new layout options and modifying existing functionality.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.
--- /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_97_END/firefox-FIREFOX_RELEASE_97_END/devtools/client/debugger/src/selectors/isLineInScope.js+++ /root/PatchLeaks-main/products/firefox_downloads/FIREFOX_RELEASE_98_END/firefox-FIREFOX_RELEASE_98_END/devtools/client/debugger/src/selectors/isLineInScope.js@@ -2,7 +2,7 @@ * License, v. 2.0. If a copy of the MPL was not distributed with this * file, You can obtain one at <http://mozilla.org/MPL/2.0/>. */-import { getInScopeLines } from "../reducers/ast";+import { getInScopeLines } from "./ast"; import { getVisibleSelectedFrame } from "./pause"; // Checks if a line is considered in scope
Analyzing the provided code diff for security fixes:
1. Vulnerability Existed: no
[Dependency Path Vulnerability] [devtools/client/debugger/src/selectors/isLineInScope.js] [Lines 2]
[Old Code] `import { getInScopeLines } from "../reducers/ast";`
[Fixed Code] `import { getInScopeLines } from "./ast";`
Additional Details:
- The change appears to be a simple module import path correction, moving from a relative path "../reducers/ast" to a local path "./ast".
- There's no clear security vulnerability being fixed here - this seems like a code organization/refactoring change rather than a security patch.
- No known vulnerability name is associated with this type of change.
Note: While path changes can sometimes relate to security (like preventing path traversal), in this case it appears to be a simple refactor within the same codebase with no security implications.
If an attacker could control the contents of an iframe sandboxed with <code>allow-popups</code> but not <code>allow-scripts</code>, they were able to craft a link that, when clicked, would lead to JavaScript execution in violation of the sandbox. This vulnerability affects Firefox < 98, Firefox ESR < 91.7, and Thunderbird < 91.7.